In our last blog post, we talked about the importance of safeguarding the aerospace and defense supply chain. For companies working with these industries, it is also critical to have strong cybersecurity regulations and protocols set in place to ensure that any sensitive information is being handled properly.
Cybersecurity Regulations
 Another increasingly vital DFAR regulation covers cybersecurity and the handling of sensitive information, namely DFAR 252.204-7012. This regulation is intended to safeguard protected defense information and ensure reporting of cyber incidences. The DoD amended DFARS in 2016 to provide for safeguarding of controlled unclassified information when residing on or transiting through a contractor’s internal information system or network. In addition DoD contractors are obligated by DFARS 70 Series regulations to ensure cybersecurity requirements are being met by all subcontractors. This means that subcontractors must comply with the NIST SP 800-171 and emerging Cybersecurity Maturity Model Certification regulations (CMMC), make enough progress on Plan of Actions and Milestones (POA&Ms), and have their current assessment results posted in the Government's Supplier Performance Risk System (SPRS).
Another increasingly vital DFAR regulation covers cybersecurity and the handling of sensitive information, namely DFAR 252.204-7012. This regulation is intended to safeguard protected defense information and ensure reporting of cyber incidences. The DoD amended DFARS in 2016 to provide for safeguarding of controlled unclassified information when residing on or transiting through a contractor’s internal information system or network. In addition DoD contractors are obligated by DFARS 70 Series regulations to ensure cybersecurity requirements are being met by all subcontractors. This means that subcontractors must comply with the NIST SP 800-171 and emerging Cybersecurity Maturity Model Certification regulations (CMMC), make enough progress on Plan of Actions and Milestones (POA&Ms), and have their current assessment results posted in the Government's Supplier Performance Risk System (SPRS).
The DoD launched the Cybersecurity Maturity Model Certification directives in 2020 due to the ever increasing need to improve the protection of controlled unclassified information (CUI) within the supply chain. The CMMC procedures incorporate five maturity levels:
CMMC Level 1
- Meeting the basic requirements to protect Federal Contract Information (FCI):
- An up-to-date antivirus software application
- Strong passwords
- Unauthorized third-party protections
- FCI is not intended for public release.
- Minimal efforts required to strengthen cybersecurity defenses.
CMMC Level 2
- Introducing Controlled Unclassified Information (CUI).
- Standard cybersecurity practices, policies, and strategic plans.
- Major subset of the security requirements specified in NIST SP 800-171.
- 55 new practices for a total of 72 total practices.
CMMC Level 3
- Good cyber hygiene and controls necessary to protect CUI.
- Continuous review of all activities based on their cybersecurity policy.
- All requirements specified in NIST SP 800-171 and other similar standards.
- 130 required security controls, grouped into 17 domains.
CMMC Level 4 and Level 5
- Addressing the changing tactics, techniques, and procedures used by Advanced Persistent Threats (APTs).
- Proactive cybersecurity program and standardized processes to achieve consistency across the entire organization.
- 171 security controls, which are grouped into 17 domains.
The DoD developed the CMMC framework to assess and improve cybersecurity posture in all tiers of the supply chain. Depending on a particular business and their position in the chain is what determines which CMMC Level is appropriate for them.
To ensure the final product complies with government regulations and customer requirements, these and other standards must be closely followed across the entire supply chain and throughout the production process. As indicated above this ranges from raw materials to vendor selection and monitoring. Stringent controls, up to date documentation, and efficient oversight are essential to ensure compliance. Without adhering to these standards and regulations critical data may be misinterpreted or worse; be leaked to unauthorized personnel or countries.
As with all certifications and compliances, there are costs associated with compliance to Cybersecurity Maturity Model Certification. For SMB companies the total cost of ownership for CMMC involves:
- Program Development & Management
- Technology & Engineering Implementation
- Audit & Certification
Costs for the various levels and their annual recurring events for SMBs are shown in the table below: 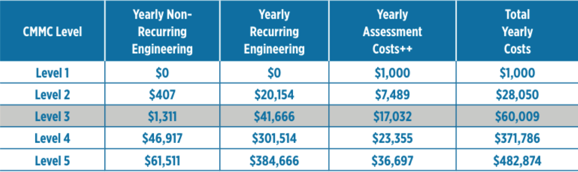
**Assessment costs consist of contractor support for pre-assessment preparations, the actual assessment, and any post-assessment work. These costs also include an estimate of the potential C3PAO costs for conducting CMMC Assessment, which are comprised of labor for supporting pre-assessment preparations, actual assessment, and post-assessment work, plus travel cost. *Defense Federal Acquisition Regulation Supplement: Assessing Contractor Implementation of Cybersecurity Requirements (DFARS Case 2019-D041)
Table courtesy of Ignyte Assurance Platform
Along with a strong supply chain and cybersecurity regulations, it's also critical for the aerospace and defense industry to be Nadcap accredited. Our next blog will cover what it means to be Nadcap compliant, and what Nadcap covers for companies working with these industries.
This blog is an excerpt from our whitepaper, The Critical Nature of Aerospace & Defense Certifications and Regulations. Click here to download your free whitepaper!
Click below to browse more of our Aerospace & Defense content.


.png)